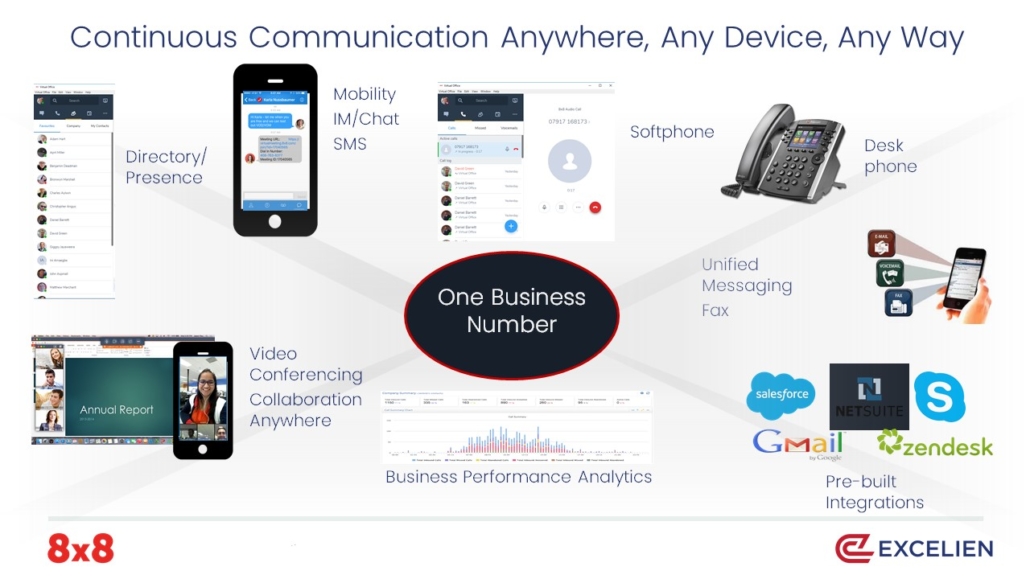
Did you know companies typically lose up to 35% of their cloud budget on idle compute resources?
Often, these unused resources stem from locked-in commitments—those reserved instances bought at a discount for periods of one or three years. Particularly for products like Azure Compute Reservations (VM RIs), where savings with on-demand prices can be substantial, the cost of unutilised commitments can really add up.
As of July 1, 2024, Azure plans to remove the ability to exchange these compute reservations, heightening the risk of financial lock-in and wasted budgets.
Now, the exciting part! Microsoft is providing a grace period for those who act quickly. Any Azure VM RIs purchased before the July 1 deadline will be eligible for a one-time exchange during their term. This allows you to tweak your reservation’s details—including family, series, version, SKU, region, quantity, and term—to better meet your evolving needs.
Take Full Advantage of Your Azure Compute Savings and Prepare for Upcoming Changes
Enter the Excelien FinOps Team. Our platform is your key to unlocking maximum savings in the cloud. We provide smart planning, procurement, and lifecycle management for Reserved Instances and Savings Plans. By leveraging the RI exchange opportunities and transitioning from RIs to Savings Plans, we craft a commitment portfolio optimised for flexibility, ensuring significant savings over the next three years—savings that would be unattainable post-July 1.
Remember, once this grace period concludes, any Azure VM RI purchases will remain fixed for their entire term. This rigidity will prevent you from adapting to new VM releases or swapping out less useful RIs for ones that better fit your needs, potentially leading to escalated costs.
Don’t let this happen to you-act now to secure your cloud savings and adaptability.
Still unconvinced? We’ve crunched the numbers: Azure RIs typically deliver 10-20% more savings than Savings Plans. With the upcoming exchange opportunity, you could boost your RI coverage by an additional 5-10%, culminating in a total savings boost of 10-25% over three years, all while mitigating the risk of over-commitment.
How Does Excelien Elevate Your Cloud Strategy?
Using a blend of automation, expert cost management, and machine learning algorithms trained on over $1 billion in managed commitments, Excelien adjusts your coverage dynamically to match your actual usage. The platform focuses on securing flexible commitments that can be adapted or exchanged to align more closely with your needs. By optimising utilisation, Excelien not only minimises reliance on expensive on-demand resources but also curtails commitment waste. Your portfolio, managed by Excelien, is engineered for maximum adaptability and minimal risk. Plus, Excelien continuously monitors exchange options and keeps an eye on Microsoft’s 12-month rolling cancellation window to ensure your Azure commitments are always at peak optimisation.
Excelien is already configured to capitalise on Azure’s VM RI exchange opportunity.
By signing up now, your commitment portfolio is automatically optimised to benefit from this limited-time offer for the next three years.
Act Fast—Here’s Why: The sooner Excelien starts managing your commitment portfolio, the better positioned you’ll be when the July 1 exchange cutoff arrives. Azure customers must act now to ensure Excelien can fully leverage this fleeting opportunity.